New Cryptocurrency Mining Campaign Targets Linux Systems and IoT Devices | CPT PPP Coverage
Cryptopolytech (CPT) Public Press Pass (PPP)
News of the Day COVERAGE
200000048 – World Newser
•| #World |•| #Online |•| #Media |•| #Outlet |
View more Headlines & Breaking News here, as covered by cryptopolytech.com
New Cryptocurrency Mining Campaign Targets Linux Systems and IoT Devices appeared on thehackernews.com by The Hacker News.

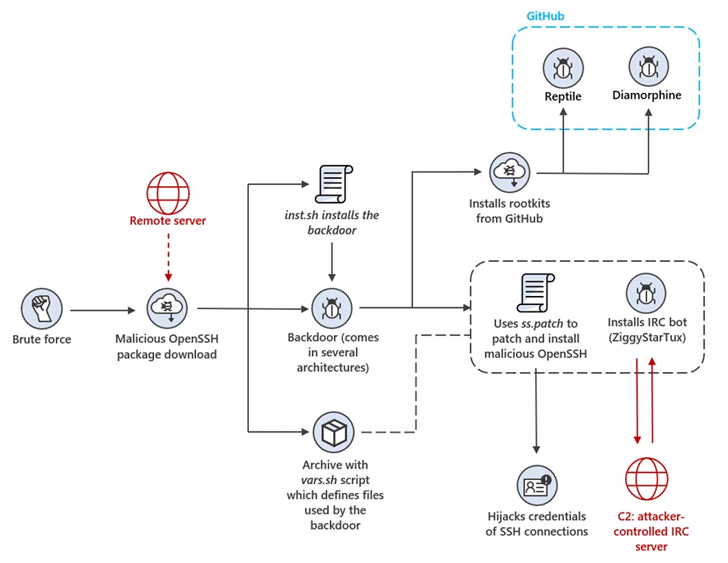
Internet-facing Linux systems and Internet of Things (IoT) devices are being targeted as part of a new campaign designed to illicitly mine cryptocurrency.
“The threat actors behind the attack use a backdoor that deploys a wide array of tools and components such as rootkits and an IRC bot to steal device resources for mining operations,” Microsoft threat intelligence researcher Rotem Sde-Or said.
“The backdoor also installs a patched version of OpenSSH on affected devices, allowing threat actors to hijack SSH credentials, move laterally within the network, and conceal malicious SSH connections.”
To pull off the scheme, misconfigured Linux hosts are brute-forced to gain initial access, following which the threat actors move to disable shell history and fetch a trojanized version of OpenSSH from a remote server.
The rogue OpenSSH package is configured to install and launch the backdoor, a shell script that allows the attackers to distribute additional payloads and conduct other post-exploitation activities.
This includes exfiltrating information about the device, installing open-source rootkits called Diamorphine and Reptile from GitHub, and taking steps to obscure its activity by clearing logs that could alert its presence.
“To ensure persistent SSH access to the device, the backdoor appends two public keys to the authorized_keys configuration files of all users on the system,” the Windows maker said.
The implant also seeks to monopolize the infected system’s resources by eliminating competing crypto mining processes that may be already running on it prior to launching its miner.
Furthermore, it runs a modified version of ZiggyStarTux, an IRC-based distributed denial-of-service (DDoS) client that’s capable of executing bash commands issued from the command-and-control (C2) server. It’s based on another botnet malware called Kaiten (aka Tsunami).
The attacks, the tech giant noted, leverage an unnamed Southeast Asian financial institution’s subdomain for C2 communications in an attempt to disguise the malicious traffic.
It’s worth pointing out that the modus operandi detailed by Microsoft overlaps with a recent report from the AhnLab Security Emergency Response Center (ASEC), which detailed attacks targeting exposed Linux servers with crypto mining malware and a Tsunami botnet variant dubbed Ziggy.
The operation has been traced back to an actor named asterzeu, who has offered the toolkit for sale on the malware-as-a-service market. “The complexity and scope of this attack are indicative of the efforts attackers make to evade detection,” Sde-Or said.
The development comes as multiple known security flaws in routers, digital video recorders, and other network software are being actively exploited by threat actors to deploy the Mirai botnet malware, according to Akamai and Palo Alto Networks Unit 42.
“The Mirai botnet, discovered back in 2016, is still active today,” Uni 42 researchers said. “A significant part of the reason for its popularity among threat actors lies in the security flaws of IoT devices.”
“These remote code execution vulnerabilities targeting IoT devices exhibit a combination of low complexity and high impact, making them an irresistible target for threat actors.”
FEATURED ‘News of the Day’, as reported by public domain newswires.
View ALL Headlines & Breaking News here.
Source Information (if available)
This article originally appeared on thehackernews.com by The Hacker News – sharing via newswires in the public domain, repeatedly. News articles have become eerily similar to manufacturer descriptions.
We will happily entertain any content removal requests, simply reach out to us. In the interim, please perform due diligence and place any content you deem “privileged” behind a subscription and/or paywall.
CPT (CryptoPolyTech) PPP (Public Press Pass) Coverage features stories and headlines you may not otherwise see due to the manipulation of mass media.
First to share? If share image does not populate, please close the share box & re-open or reload page to load the image, Thanks!



